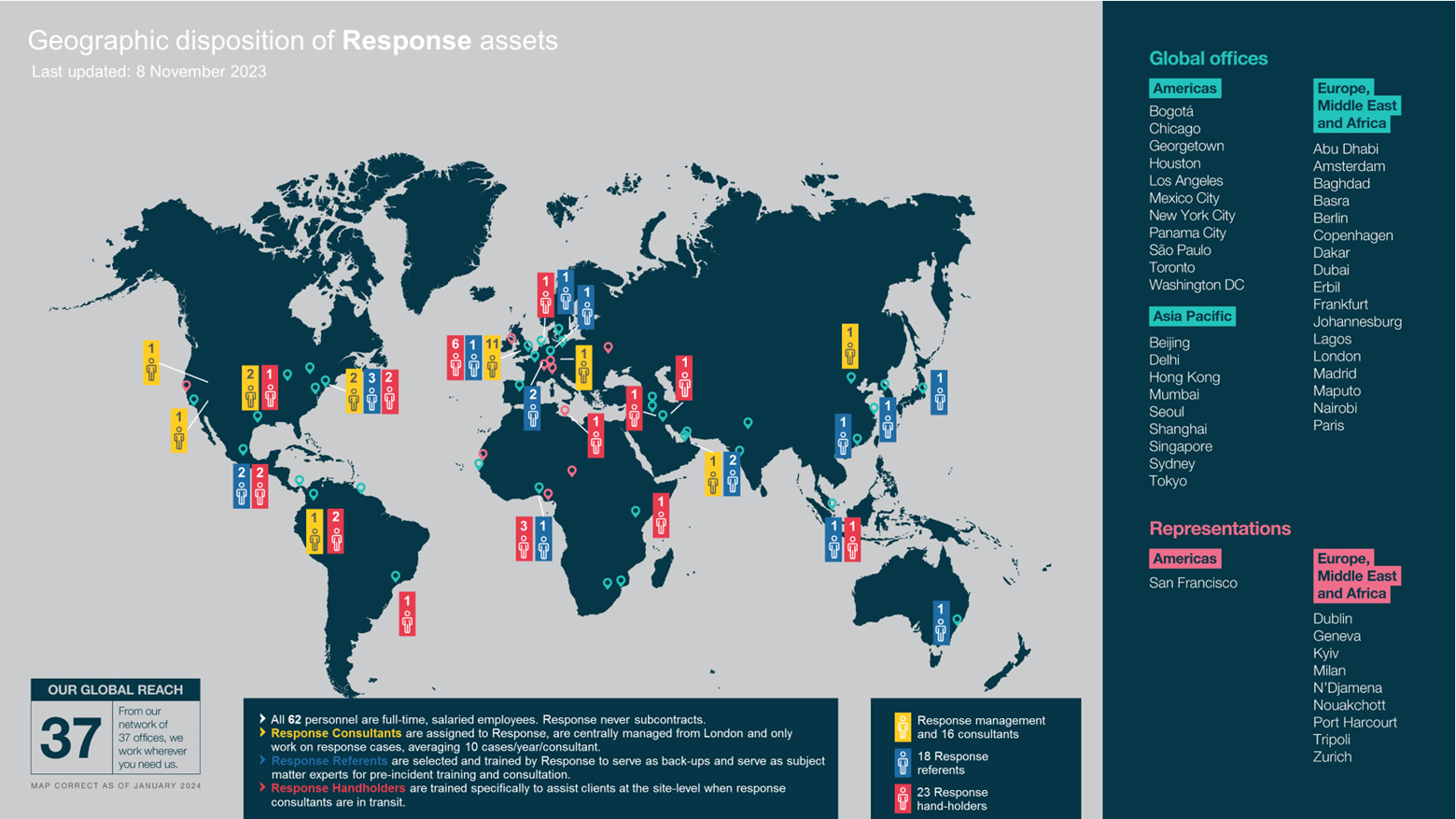
Apache Log4j Software Vulnerability

For all the great you do, please see the following insights that our Cyber Risk team believes can benefit you and your clients. This information is shared with permission from SecurityScorecard.
The recently discovered security flaw related to Log4j enables threat actors to remotely execute commands via remote code execution (RCE) on nearly any machine using Log4j. SecurityScorecard's Global Threat Intelligence team published new research on the implications of this vulnerability and what organizations can do to combat it.
The report addresses:
- The multiple avenues that threat actors might take against vulnerable servers exposed to the Internet
- Where the most frequent exploitation events are coming from
- 5 steps you should take now to protect your organization
Security Scorecard recommends taking these steps to help mitigate your exposure:
- Check if your organization is impacted: Any organization with assets running a version of Log4j above version 2.0 and below version 2.16.0 is likely impacted by the vulnerability. Review your most recent vulnerability scan results, which likely contain the location of any Log4j installations active within the environment. You can also query cloud application logs for strings matching the syntax jndi.ldap. This will identify any instances of scanning or active exploitation attempts. You can request a free Scorecard to see if a Log4j Vulnerable Version is running on your organization.
- Update to Log4j version 2.16.0 right away: The latest version can be found on the Log4j download page. Version 2.16.0 requires Java 8 or later, so make sure Java is running this version. Important: Verify that multiple Log4j installations are not present on an impacted machine, as this can mean that multiple configuration files exist. Each of these can contain a vulnerable version of Log4j. You will need to remediate each independently.
- Send our Log4Shell questionnaire to your third parties with Atlas: A new questionnaire template titled Log4Shell Questions is now available in Atlas. If you already have Atlas, you can send this questionnaire to your third parties right away. If you do not have Atlas, sign up at atlas.securityscorecard.io or watch this video and take advantage of 5 free credits that you can use to send questionnaires.
- Use the questionnaire to let your business partners know you are engaged: Leverage Atlas to proactively fill out the Log4Shell questionnaire for your own organization and share it with your business partners, letting them know what your organization is doing to address the situation. This is free and available to all SecurityScorecard customers.
- Prioritize this threat stream: Following CISA guidelines, you should ensure that you install a web application firewall (WAF) with rules that automatically update so that your SOC is able to concentrate on fewer alerts.
For additional resources, follow SecurityScorecard's blog for the latest updates and check out their FAQ in their knowledge base.
Shared with permission from SecurityScorecard.